Today, cyber security is a critical consideration for all networks. Every day, cybercriminals are finding more sophisticated ways to access and exploit networks, making protecting networks from malicious actors a top priority for all organizations.
Attack path validation is an essential security measure used to protect networks from malicious actors by identifying and mitigating potential weaknesses. If you are looking for the best Attack Path Validation you can visit https://www.picussecurity.com/.
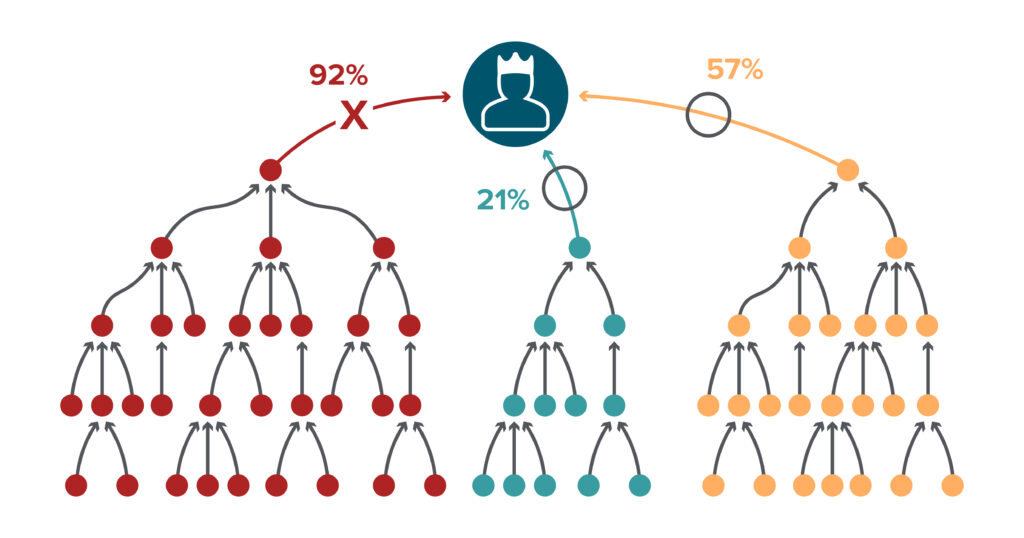
Image Source: Google
Attack path validation is a process of identifying, assessing, and mitigating the risks of attack paths. It begins by identifying the potential attack paths, or weaknesses, that exist within a network, such as unpatched software, weak passwords, and exposed ports.
Once potential attack paths are identified, the process continues with assessing the risk of each path. This assessment allows for the prioritization of different attack paths, allowing for the most pressing paths to be addressed first.
Once the attack paths are identified and assessed, mitigation strategies can be implemented to reduce the vulnerability of the network. Some common mitigation strategies include patching software, implementing strong passwords, and closing any exposed ports.
In addition, organizations can employ additional security measures such as firewalls and intrusion detection systems to further reduce the risk of attack. Attack path validation is an essential security measure for any network.
By identifying and mitigating potential attack paths, organizations can protect their networks from malicious actors and reduce the risks of cyber attacks. Organizations should take the time to identify potential attack paths, assess the risks of each, and implement mitigation strategies to ensure the security of their networks.
